Single Sign-On Best With JSON Tokens or SAML or OAuth?
Multiple accounts, fear of password loss, frustration while authenticating to online websites and applications, and bad user experience are some of the major reasons for the evolution of single sign-on solution(SSO) technology.
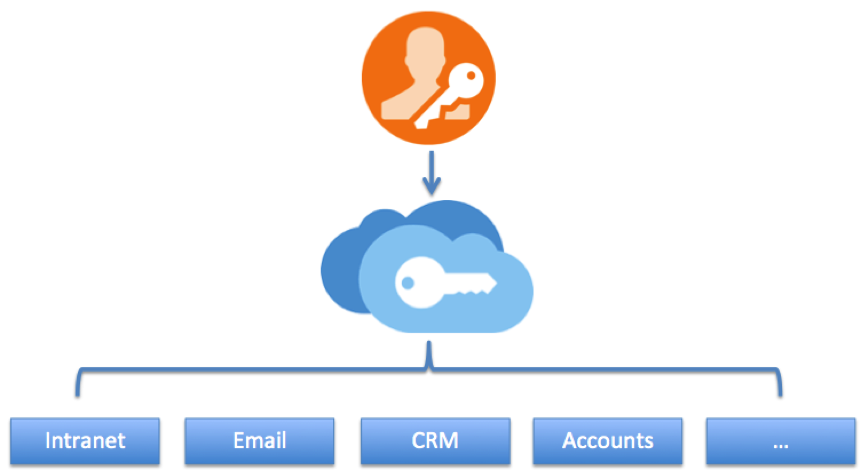
Today, most of the businesses are running multiple websites and online applications. In such situation, users have to login to each website separately with separate credentials. The SSO solution allows users to access all the websites of a business by logging in just once.
There are several implementation methods associated with the SSO. It is also available according to the size of a business (small, medium or large), by size I mean the numbers of users. This definitely raise a question, which is the one that best fits your need and niche?
To figure out the answer, here I am going to explain some of the SSO types and accentuate the concept behind different types of implantation methods (SAML and JSON).
But before diving into the article here is a brief explanation about the SSO technology.
Suppose there are three different websites website A, website B, and website C of a business. Without SSO, users have to create three different accounts for each of them and for authentication they have to type passwords of each individually. The process not only wastes their precious time but also degrades their experience. ‘
But the business can eliminate their pain by implementing SSO solution. With the solution, there is a need of single password and username for all the three websites.
Types of SSO:
Enterprise SSO: As the name suggests, enterprise sso or ESSO is an enterprise based solution. It is generally for the employees of a single business.
Web SSO: It is a solution that allows users to access different websites with single credentials of an enterprise.
Federated SSO: There are many companies that are interrelated with each other. To complete a task, users have to switch on to multiple websites of related services. Federated SSO allows them to login multiple websites of the different companies.
Now, what are the technologies that are functioning behind the working of the SSO solution?
The several implementing technologies are OAuth, SAML, and JSON Tokens.
OAuth
OAuth is not an authentication protocol but a secure authorization framework. It deals with the authorization of a third-party application to access users data without exposing their credentials. Login with G+, Facebook, Twitter in many websites and applications work under this protocol.
SAML Vs JSON web token
Both are the different protocols. But the question is, which one is best. Interestingly, the question has no specific answer. Both may be right or wrong, depends on the requirement of a business.
SAML is an XML-based solution and XML is a sort of enterprise markup language with lots of benefits. It provides lots of information to a business. But for many businesses, all the information is not necessary. For small businesses, it is like carrying a heavy suitcase for a two-day business trip.
On the other hand, JSON web token is lighter and easy to handle. It is compatible with Javascript which is currently ruling the web. Working on JSON is much easier compare to XML-based SAML solution.
So, if you are looking for a protocol for an enterprise where you require lots of information about the user and have a big user database, SAML is best for you. But if you are looking for a lightweight solution or web service, go with JSON.
Friends, these are some of the types and different protocols of a single sign-on solution. Based on your requirements and needs, choose the best service.
Similar Articles
In 2026, Microsoft Excel continues to power the U.S. business ecosystem, supporting over 80% of financial modeling, 70% of operational reporting, and nearly 65% of analyst-driven decision workflows across enterprises.
The rapidly growing volume and speed of digital transactions have had a whole lot of implications for businesses
We live in the age of cloud computing. That's plain to see. However, what may escape many are the operational and financial challenges of managing multiple independent clusters.
Times have changed and how! Take modern technology and the fast-paced digital economy, it is driving. Given the market conditions, any company's infrastructure has become more than just a technical detail.
It has been for everyone to see that the modern digital economy is distinguished by high volume, real-time financial transactions.
Business success has become reliant on efficiency and agility of the underlying technology infrastructure. Clearly, companies now depend on cloud computing to provide seamless services while managing exponential data growth.
Hospitals operate in environments where availability and patient safety are paramount at all times. As medical supply chains expand and regulatory oversight becomes more demanding, manual tracking methods introduce delays and risk.
Every sales funnel has one core goal: turn attention into revenue as efficiently as possible. Yet many funnels leak value at critical stages—visitors bounce, leads go cold, and sales teams chase prospects who were never a good fit.
Decentralized Finance (DeFi) has transformed how users earn passive income through blockchain-based financial systems. Among its most popular use cases,