How Devsecops Program Is Important For Cybersecurity In The Cloud-first Era?

In the modern era of DevOps and cloud-native applications, there has been a significant cloud paradigm shift with changing roles of IT departments and changing a line of business for business agility. Businesses around the corporate world today, use Software-as-a-service(SaaS), Infrastructure-as-a-service(IaaS) or Platform-as-a-service(PaaS), including the development of applications that use cloud-native applications and DevOps processes to expedite continuous integration and deployment. With extensive use of cloud services, cybersecurity and corporate IT is losing control over the security of cloud-delivered applications due to the blurred line of business.
Cloud-First Era:
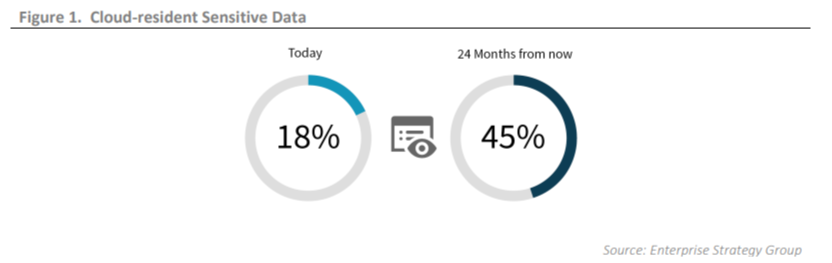
The complexion of cloud adoption has reached new heights with the wide-spread use of cloud services in different forms. Cloud is now the center of the computing universe. Broad use of SaaS and IaaS are pushing corporate data to be cloud-resident. According to a report by ESG-Enterprise Strategy Group, 24% corporates believe that 40% of their corporate data reside in cloud service, which will increase up to 58% in 2 years. Also, 18% of cloud-resident data resides in cloud-services, which will increase up to 45% in 2 years.
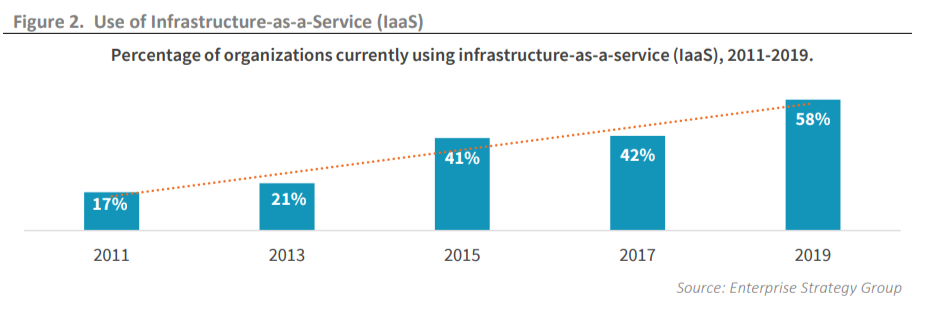
IaaS is a cloud service has seen notable growth in the use by organizations worldwide. About 42% of organizations used the IaaS service in 2017, which increased to 58% in 2019. This data represents the extensive use of cloud-service by corporates and organizations to develop software and applications.
Cloud-Native Applications:
The tight coupling of agile software development and DevOps methodologies, create seamless, cloud-native applications. The extensive use of DevOps indicates extensive use of agile software. Usage of agile and DevOps is fundamental in the application of the DevSecOps program to protect cloud-native applications. Development of DevOps and deployment of cloud-native apps is the proliferation of trusted identities and privileges like API keys, automation bots, third-party contractors, etc. These privileges pose a high-risk factor for cloud-native applications.
With the adoption of microservices for cloud-native applications, organizations are moving towards serverless operations. According to the report by ESG, 52% of organizations are using serverless functions, that expose cloud-native apps to high risks. Cloud-native applications use a heterogeneous mix of workload servers with micro-service like virtual machines, bare-metal servers, serverless functions, etc.

Top Challenges to the security of Cloud-Native Applications:
1. Maintaining security consistency across data centers and public cloud environments, where cloud-native applications are deployed.
2. The use of multiple cybersecurity controls increases costs and complexity.
3. Lack of understanding of threat type and threat vectors.
4. Non-involvement of cybersecurity by DevOps to expedite process.
5. Lack of Infrastructure activity control and visibility.
6. Using prescribed best practices for configuration of cloud-resident workloads and APIs.
7. Non-support to cloud-native applications by existing tools.
DevSecOps for secure solutions:
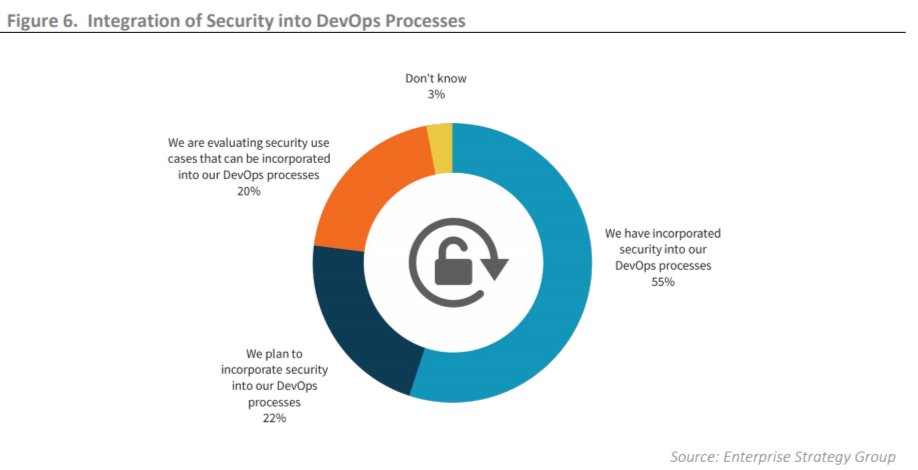
DevSecOps is a vital implementation for secured cloud-native applications, Improved security can be achieved by treating security as an immutable DevOps processes use case. Corporates can hire developers that can include initial DevSecOps use cases that were implemented in both pre-deployment and runtime stages such as workload configuration during integration and automation of applications. According to the report by ESG, 55% of corporates indicate the integration of security in the DevOps process.
Application Lifecycle Approach:
A secure DevOps program will employ DevOps friendly cybersecurity controls that integrate natively CI/CD tools( Continous integration/ continuous deployment) to secure the development, integration, test, build, delivery and runtime stages of application lifecycle. Writing secure code and shipping hardened images to production is a big part of the DevSecOps equation, but equally important are automatically applying runtime controls integration with the CI/CD orchestration tooling used to push apps to production.
Secure the Identity Perimeter:
Usage patterns and privileges by which a user access cloud-resident data is treated as an identity perimeter. To secure such perimeters, there should be a continuous discovery of data and monitoring to detect policy violations and anomalies that put perimeters at risk. Corporates and organizations should look to detect, when, where, who and how are the data accessed to provide a context to the cloud-resident data.
Defense In-Depth:
Applications are deployed in cloud platforms for auto-scaling of backend and access Content Delivery Networks (CDN) to scale front-end. To achieve these factors applications are built on native infrastructures architectures risking vulnerabilities. To protect these applications defense in-depth strategy should be used. Traditional strategies can mitigate cross-site scripting(XSS) and SQL injection attacks. In addition to these traditional strategies, behavioral-based approaches can be used to provide security from web-requests of auto-scaling groups.
Next-generation Web Apps Firewalls(WAF) and Runtime Apps Self-Protection(RASP) provide pro-active monitoring over web-request traffic. When next-generation WAF and RASP runtime analysis is compared against known good behavior of a system in question, it allows detection of malicious request indicators, to prevent the same attack pattern from impacting other users on the same service.
Optimizing the pee-level data collected from production traffic yields higher results in the detection and prevention of attacks. DevOps teams can automate web defense with high precision in production by using a next-generation WAF approach. Rather than choosing a legacy WAF vendor that relies on regular patterns matching rules and signatures.
Conclusion: The scale at which cloud services are used by organizations for various applications, pose more and more security concerns and challenges in years to come. The most rampant issue is a gap between cloud-native applications development and its security retooling needs that is now shrinking due to organizations making efforts to resort to more secure methods and tightening their monitoring and control strategies over cloud-resident data.
DevSecOps processes implementation with in-depth defense strategies can provide enhanced security to such cloud-native applications and further inclusion of cybersecurity teams into apps development lifecycle can ensure constant monitoring over data with control over visibility of each activity over cloud-resident sensitive data.
Similar Articles
Building lending software isn’t just a technical project—it’s a business decision. Whether you're a fintech founder or part of a traditional lending institution trying to go digital, three questions will shape everything that follows
Learn why robust security is crucial for super app development. Explore key strategies and best practices for mobile app development security.
Walkie-talkies with an extensive reception capacity have changed significantly when it comes to portable communication by displaying cutting-edge features with seamless connectivity that covers more than just the state
USB-C technology has revolutionized the way we charge our devices, offering faster charging speeds, higher power delivery, and universal compatibility across multiple devices
Discover expert mobile app development strategies to create a viral app that attracts users and boosts engagement
Optimize app localization for iOS users across the EU with language, cultural, and regulatory adaptations. Engage users and boost retention with these tips!
Discover the top 10 mobile app development trends of 2024! Explore 5G, AI, AR/VR, blockchain, and more to stay ahead in the ever-evolving app development landscape.
With its triple-lens design and fantastic photo and video quality, the iPhone 11 Pro Max is extensively acknowledged for its superior camera system. But problems can occur with also one of the most advanced technologies. If you're having issues with the iPhone 11 pro max camera lens, knowing the typical problems and how to repair them
Protect your app from threats with AppSealing's robust, all-inclusive security solution. Safeguard user data, ensure compliance, and maintain top performance.