Enhancing Continuity: Leveraging Advanced Data Migration Techniques

"Tenant to tenant migration" has become a pivotal aspect of organizational evolution. As companies expand, merge, or restructure, seamlessly transferring data between different instances or tenants becomes crucial for maintaining operational continuity.
This process is more than just a technical maneuver; it is a strategic move that ensures the uninterrupted flow of information, applications, and services. In this article, we delve into the intricacies of enhancing continuity through the lens of advanced data migration techniques, shedding light on the challenges, strategies, and transformative power of these processes.
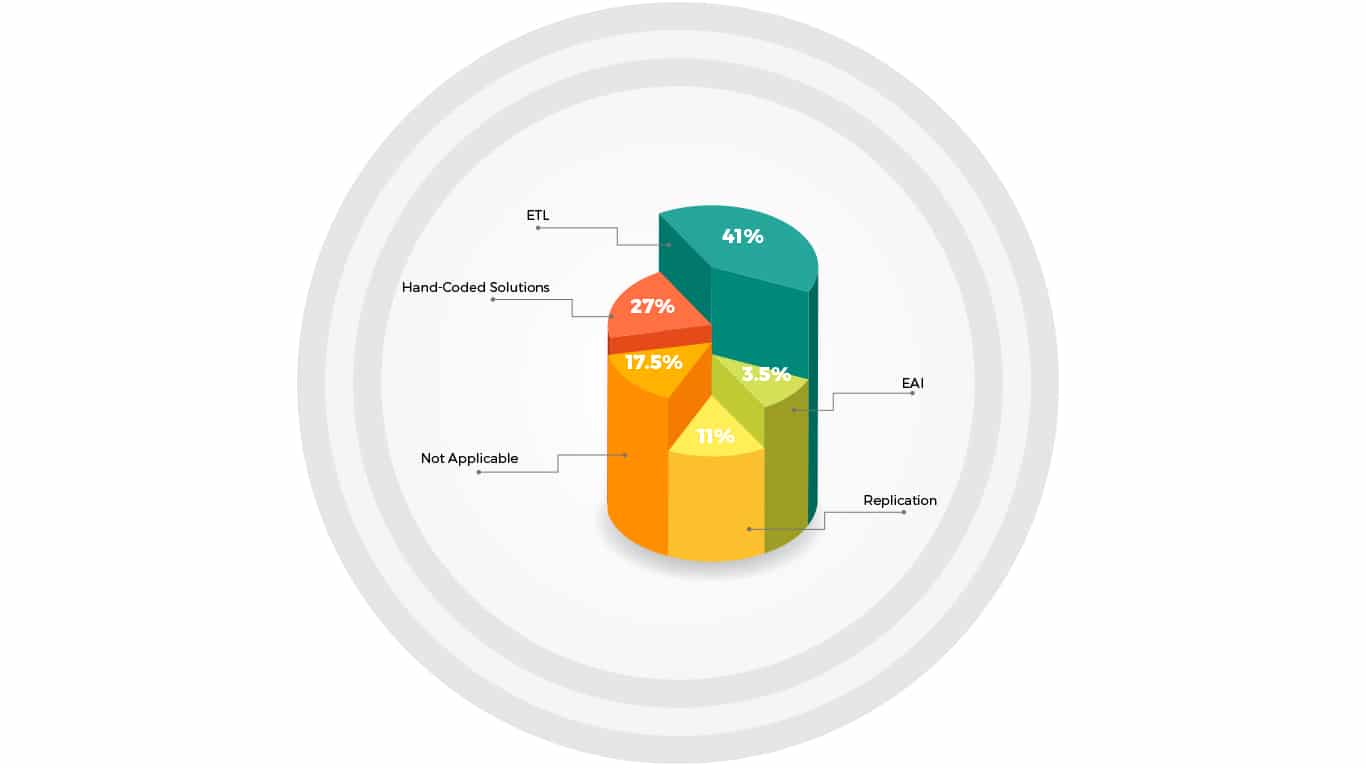
Tenant to Tenant Migration
Tenant to tenant migration, at its core, involves transferring data and applications from one instance or 'tenant' to another within a cloud environment. This process is instrumental when organizations undergo structural changes, such as mergers or acquisitions, or migrate to a new cloud service provider.
The challenges of such migrations are multifaceted, encompassing issues like data integrity, security, and the seamless transition of user access and settings. Successful execution of tenant-to-tenant migration demands a meticulous strategy that caters to these challenges while ensuring minimal disruption to regular operations.
High Stakes in Tenant-to-Tenant Migration
Tenant to tenant migration is a high-stakes operation that requires a comprehensive understanding of the existing and target environments. One of the critical aspects involves mapping data structures and dependencies accurately. This ensures data retains its integrity and relationships during migration, preventing information loss or corruption.
Additionally, thorough analysis of security measures is imperative to safeguard sensitive data during the transition. Effective tenant to tenant migration hinges on a meticulous planning phase that considers these nuances, guaranteeing a smooth and secure data transfer process.
Understanding in More Details
1. Data Mapping and Structural Integrity
Successful tenant to tenant migration commences with meticulously analyzing existing data structures. This involves mapping data dependencies, understanding relationships, and creating a blueprint for the transfer. The goal is to ensure that data retains its structural integrity during the migration, preventing loss or corruption.
2. Security Measures and Compliance
Ensuring the security of sensitive data is a paramount concern during migration. Robust encryption, access controls, and compliance with industry regulations must be seamlessly integrated into the migration process. This not only safeguards the organization's data but also instills confidence in stakeholders regarding the safety of their information.
3. User Access and Settings Transition
A smooth user access rights and settings transition is critical to maintaining operational continuity. A detailed strategy for migrating user profiles, access privileges, and application settings guarantees that employees experience minimal disruption in their workflows post-migration.
4. Downtime Mitigation Strategies
The impact of downtime during migration can be significant. Implementing effective strategies to mitigate downtime, such as phased migration or employing backup systems, ensures the organization continues its operations without prolonged interruptions.
5. Testing and Validation Protocols
Thorough testing of the migration process is indispensable. Implementing validation protocols that include simulated migration scenarios allows organizations to identify and rectify potential issues before the actual migration, minimizing the risk of unexpected disruptions.
6. Automation for Efficiency
Leveraging automation tools streamlines the migration process, reducing manual errors and enhancing overall efficiency. Automation ensures a standardized and repeatable migration procedure, making the transition more reliable and less prone to human-induced errors.
7. Stakeholder Communication and Training
Open and transparent communication with stakeholders is pivotal. Informing employees about the migration process, its benefits, and potential disruptions builds understanding and cooperation. Providing training sessions for staff ensures a smoother transition to the new environment.
8. Post-Migration Monitoring and Optimization
The migration journey does not end with the transfer of data. Implementing robust monitoring systems and optimization strategies post-migration allows organizations to identify and address any lingering issues, ensuring the new environment operates efficiently.
9. Cost-Benefit Analysis
Conducting a comprehensive cost-benefit analysis before embarking on tenant to tenant migration provides insights into the financial implications. Understanding the investment required versus the long-term benefits aids in making informed decisions and justifying the migration effort.
10. Lessons Learned and Continuous Improvement
Every migration process is a learning opportunity. After completion, organizations should conduct a detailed analysis of the migration's successes and challenges. Implementing continuous improvement strategies based on these lessons ensures that future migrations are even more streamlined and effective.
Key Considerations
Key Aspect |
Insights |
| Data Mapping | Precise mapping of data structures to ensure integrity. |
| Security Measures | Robust encryption, access controls, and compliance adherence. |
| User Access Transition | Seamless migration of user-profiles and application settings. |
| Downtime Mitigation | Strategies for minimizing downtime, such as phased migration. |
| Testing and Validation | Thorough testing and validation protocols for identifying issues. |
| Automation for Efficiency | Leveraging automation tools to streamline the migration process. |
| Stakeholder Communication | Transparent communication and training sessions for employees. |
| Post-Migration Monitoring | Implementing monitoring systems for identifying and addressing issues. |
| Cost-Benefit Analysis | Conducting a comprehensive analysis of the financial implications. |
| Lessons Learned and Improvement | Continuous improvement strategies based on migration experiences. |
Final Words
Tenant to tenant migration is not merely a technical process but a strategic initiative that demands meticulous planning and execution.
Organizations can enhance continuity and reap the benefits of a seamless migration by delving into the intricacies of data mapping, security measures, user access transition, and other key considerations.
Adopting advanced techniques, automation, and a continuous improvement mindset ensures that tenant-to-tenant migration becomes a catalyst for organizational evolution rather than a disruptive force.
Similar Articles
Digital files come in many different file formats, each with their own specific features and uses. Here we will explore some of the most common digital file types to help you understand the differences between them.
In the vast landscape of cyber threats, one adversary has emerged as a formidable force, disrupting businesses and causing chaos: ransomware. The surge in ransomware attacks has elevated the need for a robust defense strategy.
The prospect of migrating critical systems and data to the public cloud understandably raises concerns. Will valuable assets end up exposed or locked in?
In today's data-driven world, organizations constantly seek ways to visualize and analyze their data to make informed decisions. Two popular tools in the business intelligence (BI) space are Microsoft's Power BI and Tableau. Both of these tools offer powerful features for data visualization, data modeling, and data analysis
Healthcare organizations collect and store an immense amount of data. The data is essential for doctors to make informed decisions about patient care. However, the sensitive nature of this data requires healthcare organizations to protect it from unauthorized access and data breaches.
Every firm nowadays is establishing its presence in the digital sector to grow internationally. As many might know in the technological environment, web development is essential for success.
One of the things that distinguish having the CIO position now from having the job in the past, apart from the increasing recognition of the significance of information technology, is the introduction of so-called "big data." We're talking about terabytes or even petabytes of data, as well as all of the problems that come with managing such a large amount of data.
A computer virus is a program that is loaded in a system without the knowledge of the user. This virus is not formed naturally but it is induced by people. After entering your system, it gets attached to another program and as the host starts working, the virus starts functioning.
Looking to buy the gaming chair? You’re standing at the right place. The gaming chair offers an immersive media X-perience as they generally put you closer to the TV and therefore closer to the action.